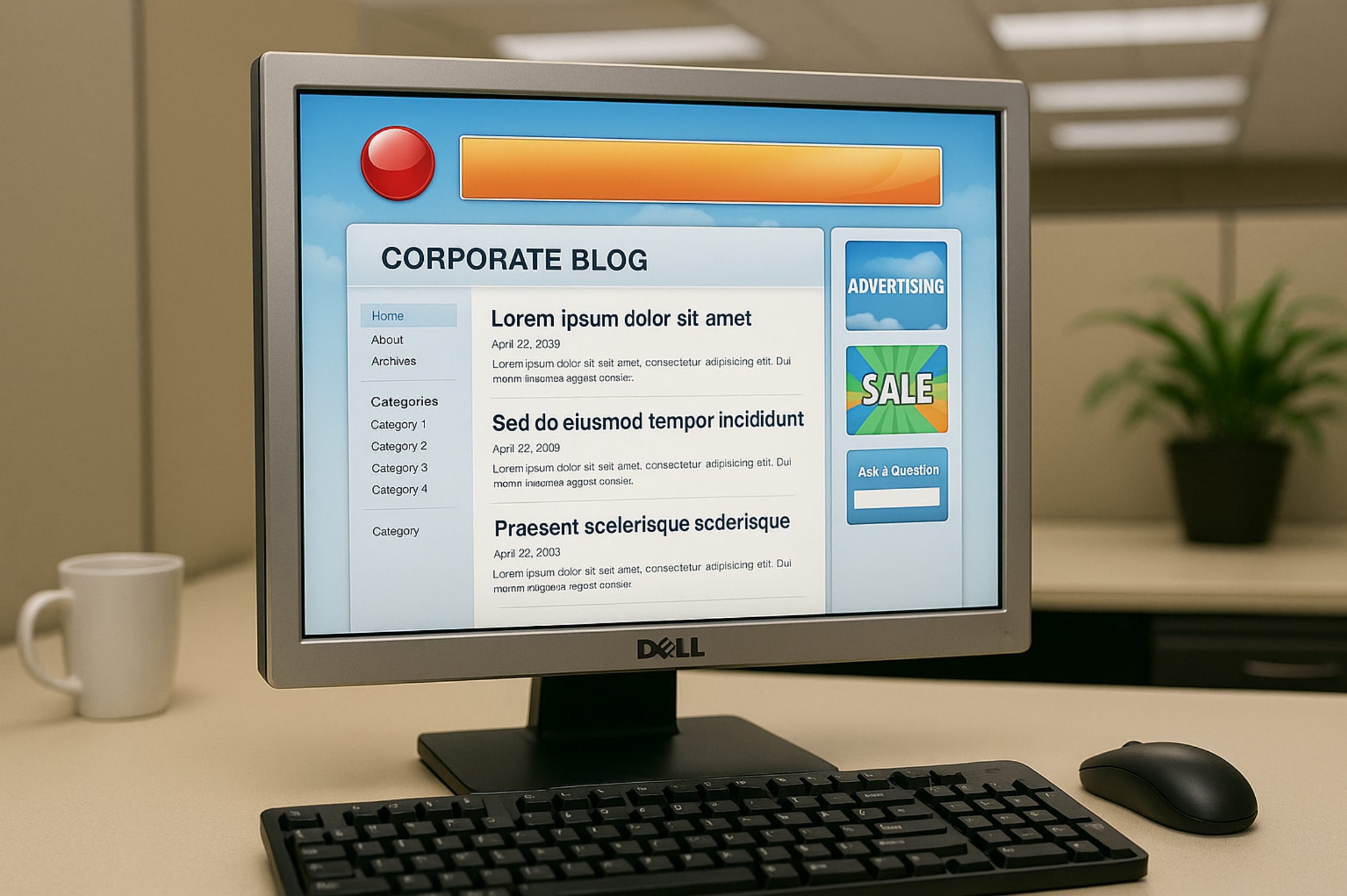
Brazil's First Telecom Corporate Blog
Why we built our own CMS instead of using WordPress—and how it survived 5 years of attacks
Context
In early 2008, I was brought in as a technical consultant to one of Brazil's largest telecommunications companies. They'd just completed a massive brand unification across 18 Latin American markets and were racing to launch 3G services. The brief was ambitious: build Brazil's first telecom corporate blog platform that could handle dialogue with 30 million potentially vocal customers.
My role was to architect and oversee the platform build, working with their internal IT teams and external vendors. The CEO's vision was clear—transform customer communication from one-way press releases to genuine two-way engagement. My contract success metrics included platform stability, security, and launching within 90 days.
The Challenge
During discovery, I evaluated the obvious choice: WordPress. It powered 60% of blogs globally and had strong community support. But my security assessment revealed critical concerns for an enterprise telecom deployment:
The WordPress Security Landscape (2008):
SQL injection vulnerabilities discovered monthly
Plugin ecosystem full of unvetted code and backdoors
No enterprise security tools (WAFs, automated scanning)
Core platform updates often broke customizations
Recent high-profile breaches at major WordPress sites
For a company in the middle of a massive rebranding initiative, any security incident would be catastrophic. A hacked blog displaying defaced content or spreading malware would undermine millions spent on brand unification. In 2008, WordPress was like hosting your grand reopening in a venue with broken locks.
Part of my security strategy was complete isolation—the blog infrastructure would have zero access to corporate networks or customer data. Air-gapped security by design. This reduced attack surfaces and compliance scope, but it didn't reduce the brand risk of a compromised public platform.
My recommendation shocked the project’s board: build custom. They hired me for expertise, not to reinvent wheels. But sometimes the available wheels don't fit your race car.
The Approach
I designed a security-first architecture using enterprise-grade components:
Technical Architecture:
Platform: ASP on IIS (leveraging existing Microsoft licenses)
Database: SQL Server with encrypted connections
Custom CMS: Purpose-built for blogging with strict security controls
Infrastructure: Load-balanced cluster with automated failover
Key Design Decisions:
Bulletproof Security: Every input parameterized, every output encoded. Multiple validation layers—if hackers breached one, others would stop them. No dynamic SQL, no exceptions.
Intelligent Cache Invalidation: I architected a granular caching system that could serve millions of requests while maintaining real-time updates. Instead of clearing entire caches, we surgically invalidated only affected segments.
High Availability Cluster: Three active nodes behind hardware load balancers. Each node could handle 100% traffic. Real-time database replication ensured zero data loss during failovers.
The Execution
Week 1 - Attack of the Bots: Our honeypot URLs (common WordPress paths returning 404s) logged 10,000+ automated attack attempts. The bots expected WordPress vulnerabilities and found... nothing. Security by obscurity? No—security by not being WordPress.
Week 3 - Load Testing Results: Initial load tests with 10,000 concurrent users showed page response times of 3 seconds—below our performance targets. After analyzing the metrics, I identified cold cache issues and implemented a cache warming strategy. Response times immediately dropped to 300ms, exceeding our performance SLA by 3x.
Month 1 - The Comment Tsunami: The 3g data plan announcement generated 3,000 comments in four hours. Our caching strategy didn't just survive—it thrived. Competitors' WordPress sites crashed under similar load.
Month 2 - Scaling Content Management: As content volume grew, the editorial team needed better tools for scheduling and managing posts. I implemented a workflow system with draft/review/publish states, scheduled publishing, and role-based permissions. The system could handle multiple authors and editors working simultaneously without conflicts. This became crucial when the marketing team wanted to coordinate blog posts with product launches across different time zones.
Month 3 - Human Touch at Scale: I trained content moderators on efficient workflow. They responded to every comment within 24 hours by creating response templates and escalation procedures. Engagement skyrocketed—customers couldn't believe a telecom actually listened.
The Reckoning
Delivered Results:
1.2 million unique visitors, Year 1
99.98% uptime vs. 99.5% SLA
Zero security breaches over 5-year lifespan
35% call center reduction for blog-covered topics
Industry award for customer engagement innovation
Contract extended 3 times for platform enhancements
What Worked Brilliantly:
Custom security avoided every major vulnerability that hammered WordPress (2008-2013)
Cache invalidation strategy became a competitive advantage during crisis communications
Direct system integration enabled features competitors couldn't touch
What I'd Do Differently:
Better content workflow tools: I underestimated how much editors would need. The simple interface became a bottleneck as content types evolved.
Mobile-first missing: By 2010, mobile exploded. Our desktop-optimized design needed expensive rework.
Knowledge transfer gaps: I documented code well but not architectural decisions. When I rolled off, tribal knowledge walked out with me.
Should have productized the caching layer: Other clients could have benefited from our invalidation strategy.
Why not WordPress?
In 2008, WordPress was a security nightmare for enterprise deployment. Today? Different story—managed WordPress hosting offers enterprise-grade security. But back then, building custom was the only responsible choice for a telecom handling millions of customer records.
Expensive Lessons Learned:
Sometimes "Not Invented Here" is the right choice. When existing solutions don't meet security requirements, building custom isn't ego—it's engineering.
Cache invalidation remains one of CS's two hard problems. But solve it well, and you've got a moat competitors can't cross.
Security paranoia pays dividends. Every Brazilian bank and telecom was under constant attack in 2008. Being unhackable became a marketable asset.
Consultants must balance innovation with knowledge transfer. The platform succeeded, but I failed to make the client self-sufficient in evolving it.
The lesson? Technology decisions must fit the specific moment, requirements, and risks. In 2008, for a Brazilian telecom under constant attack, building a custom fortress beat decorating someone else's house—even if that house was the neighbourhood favourite.